Why Phone Record Breaches Increase Risk of Impersonation Scams
The AT&T phone record breach – which took place in 2022 and was disclosed July 2024 – affects everyone. Even if you're not an AT&T customer,...
Five Nines Team : Jul 16, 2024 9:44:19 AM
2 min read
According to Verizon’s 2024 Data Breach Report, 68% of breaches in 2023 involved a non-malicious human element, like a person falling victim to a social engineering attack or making an error. It can take just one simple slip-up from an employee at any level in an organization to open a door for attackers.
Maintaining strong security awareness at the user level is one key step toward keeping your organization's valuable data safe.
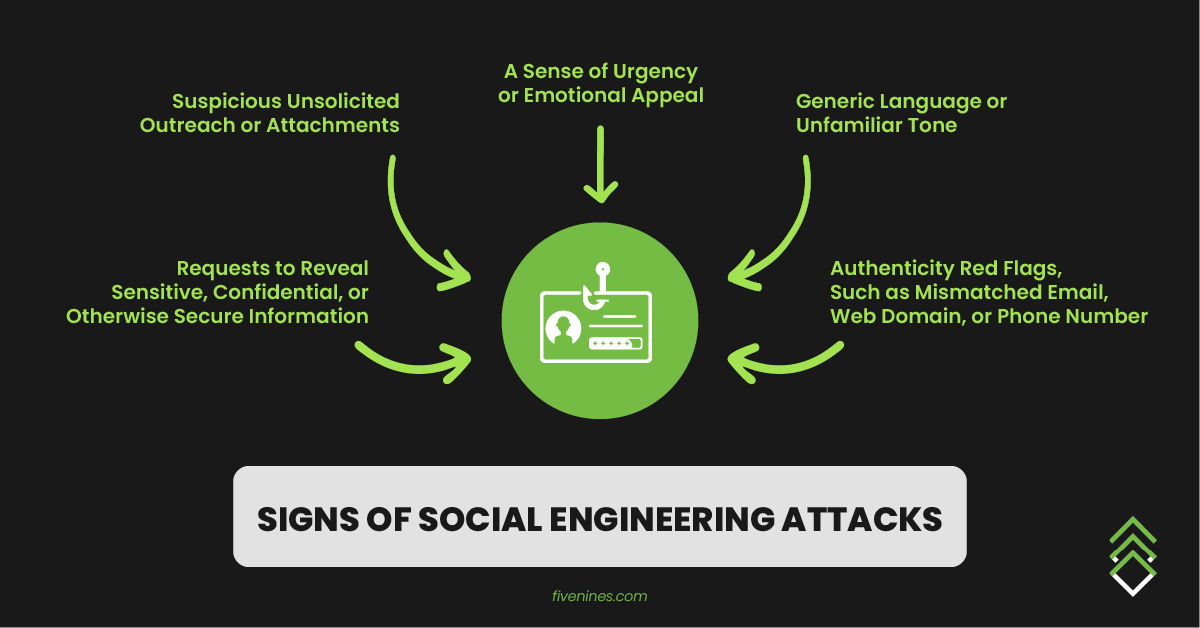
Here are the top 5 indicators of social engineering attacks to keep in mind when interacting with emails, phone calls, texts, or even social media communications.

If you don’t usually receive requests to wire money or share sensitive info, then an email or phone call asking you to transfer funds should be an easy red flag.
For any unexpected request – whether by email, call, or text – stop and ask yourself if the request makes sense before you click a link, open an attachment, respond to a message, or provide any data verbally or digitally.
If you’re unsure, or if something seems suspicious, try contacting the sender in person. If that’s not possible, search the organization online and use the official contact information from their website to get in touch and verify the unusual request.
Before you click a link or open an attachment in email or text, check for a few red flags.
First, unless you have specifically requested such file, steer clear of any file attachment ending in .exe. However, know that malicious files come in all shapes and sizes. A .exe file is a clear sign of danger, but malicious code and viruses can hide in nearly any type of file, including Microsoft documents and PDFs. Play it safe and avoid opening any unexpected attachments.
Also, be aware of links that look familiar or trustworthy but are malicious-in-disguise. Hover over links before clicking, and double-check that the destination of the link is a trustworthy site as well. When in doubt, just don’t click!
“Urgent!”, “Action Required!”
While there may be times that a business or individual needs you to take an immediate action, their subject lines would likely be a bit more specific. It’s in your best interest to be suspicious of any communication that uses red-alert terms or encourages you to feel rushed, stressed, or concerned.
It's safe to be suspicious when the language of a message isn’t quite right – for example, a coworker suddenly communicating more casually than normal, or a family member acting far too formal.
In addition to suspicous tone, be critical of communications from “trusted” brands or organizations that don’t address you by name—especially if the message is about account information or other sensitive data. Things like “valued customer” and “user” may seem innocuous or even standard, but in many cases, a non-personalized greeting is actually a sign of trouble.
If a communication seems strange, it’s worth looking for other indicators that it could be an impersonation scam.
Remember an earlier time, when you were once told not to trust strangers on the internet? Cybercrime goes beyond targeting young users on messaging forums, and the risks are just as prevalent among other digital communication methods these days.
Turning a critical eye on a sender’s address or contact number can help you identify the first sign of a phishing email, text, or call. Watch out for specific red flags in email addresses, such as an illegitimate or unfamiliar domain, or display names that don’t match the email address behind them.

The AT&T phone record breach – which took place in 2022 and was disclosed July 2024 – affects everyone. Even if you're not an AT&T customer,...

Support for Microsoft Windows 10 ends October 14, 2025. After this date, Microsoft will no longer provide free security updates, patches, or any...

SMS phishing (“smishing”) is a form of phishing in which an attacker uses SMS text messages to trick recipients into taking an action and...